Jvoisin and Maijin, a members of my hackerspace (Hackgyver) always talk to me about Radare, a new reverse engineering open source framework which they are working on.
So i want to try it on a very simple Linux crackme.
Classic and easy install, download it to the git, configure, make and make install.
The condemned binary’s called “Easy_ELF”
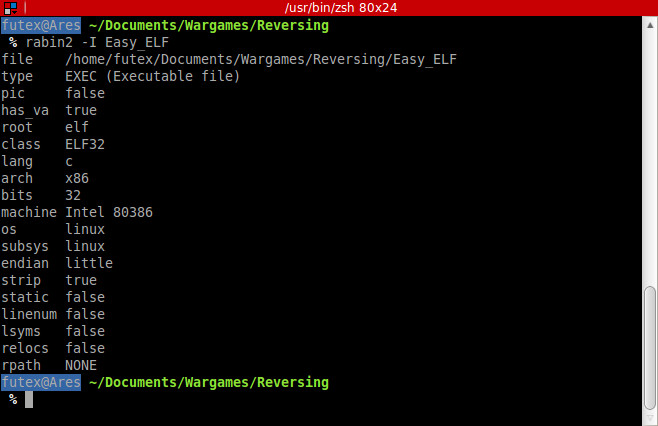
Start to see who is it
Sections:
I want to see it’s strings.
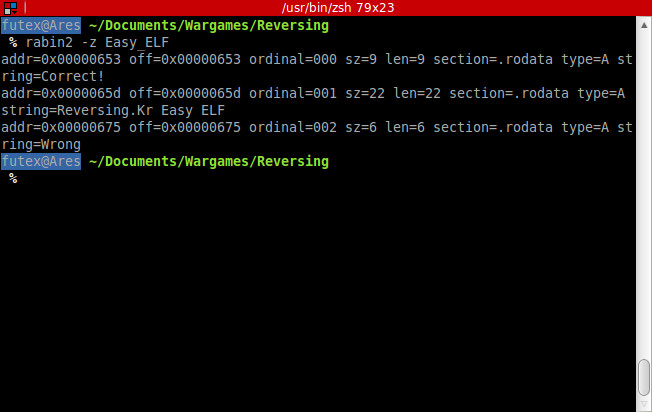
We have the good and bad boy and they offset 🙂
Try to launch the crackme:
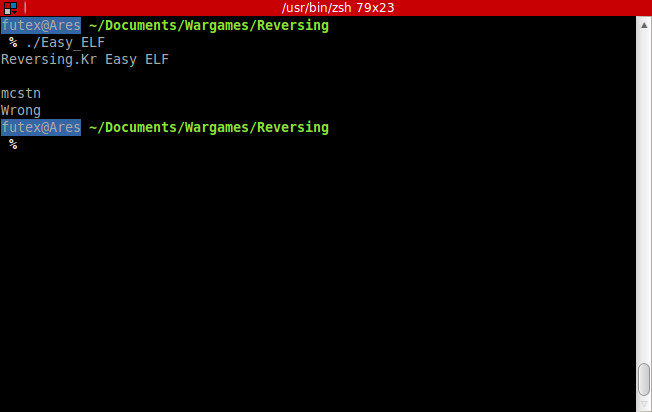
Ok, we can start static analysis, disassemble the 15 first lines
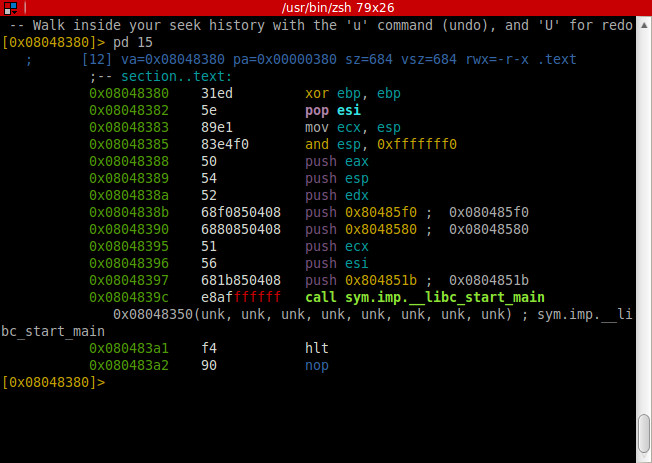
We arrive to the start function and we can see the main function start at 0x804851b.
Show the 30 first lines of the main function
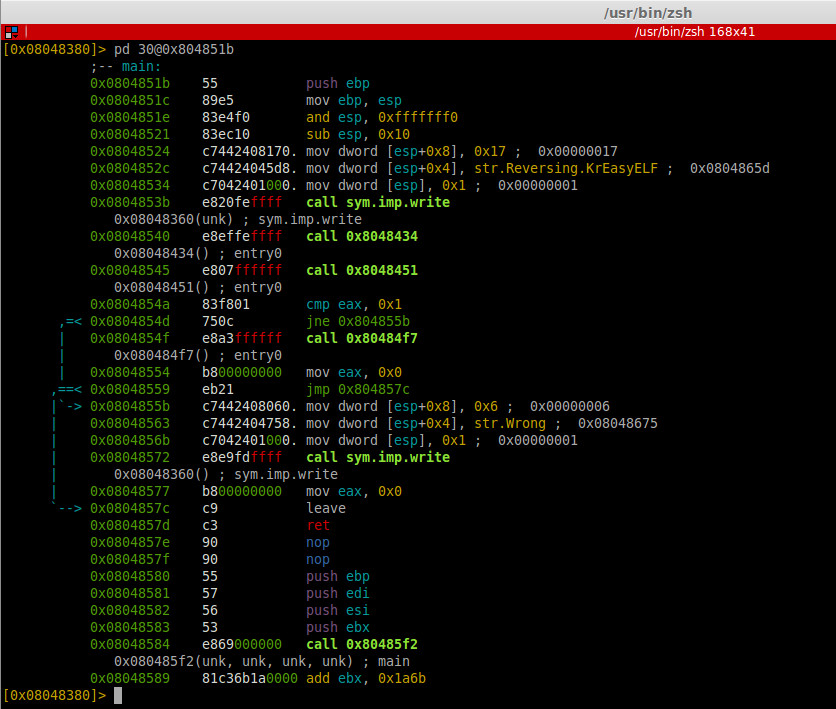
We assumed the password check function is at 0x8048451
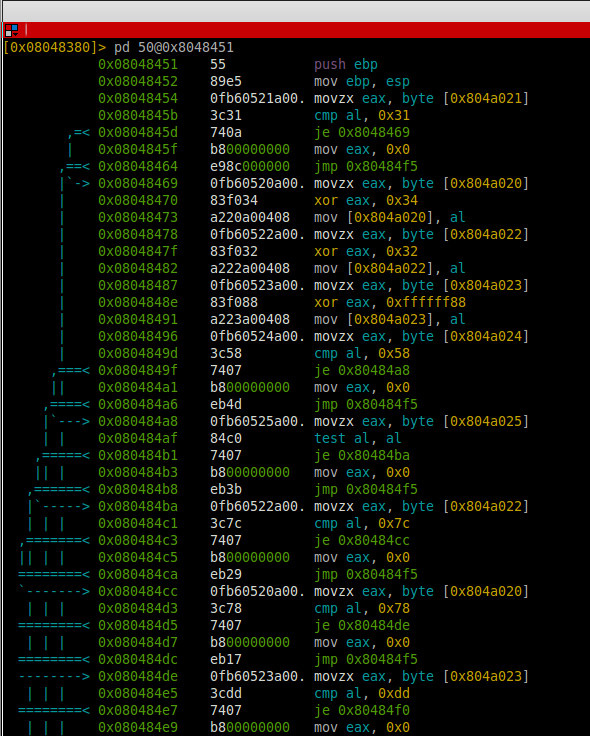
The first cmp compare the second letter of the pass with 0x31, an the fifth with 0x58.
All other characters is just xored.
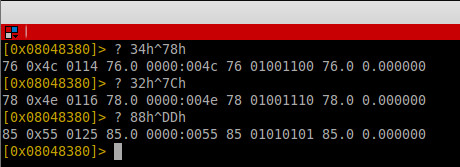
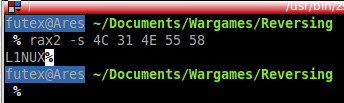
We have 0x4C 0x31 0x4E 0x55 0x58
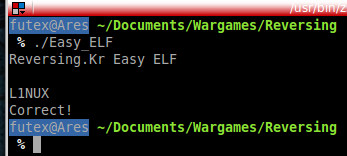
\o/
Radare support many architectures arm,x86, x86-64, gameboy, mips, sparc,… and many type of files, dex, bios, elf, PE, COFF. Radare team make a great work!
So, i have try 1% of all Radare possibility the 99% others is here:
