A few days ago, i receive a weird connection on my kippo honeypot.
An guy as connected on, download a binary file and try to lauch it, but, not succesfully.
So after some checks, i can download this binary :), so, go to analysis it!
$ file disknyp
disknyp: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, for GNU/Linux 2.2.5, not stripped
$ du -sk disknyp
1460 disknyp
It’s statically linked, that’s explain is big size, and it’s not stripped 🙂
Hash:
MD5: 260533ebd353c3075c9dddf7784e86f9
SHA1: 9a40f162e5bcaac2d58c0363ef2baf7b4c1a9710
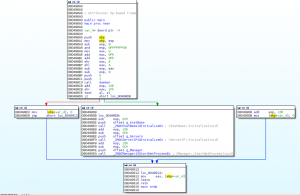
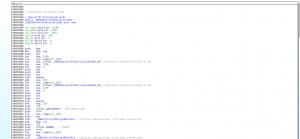
Look at the main function in IDA.
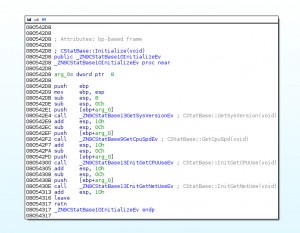
Coded in C++, it run as a daemon, after, it lauch _ZN9CStatBase10InitializeEv who get some system infos.
_ZN9CStatBase13GetSysVersionEv do a uname command.
_ZN9CStatBase9GetCpuSpdEv get cpu info to /proc/cpuinfo and extract frequency.
__ZN9CStatBase13InitGetCPUUseEv open /proc/stat file and check cpu usage.
_ZN9CStatBase13InitGetNetUseEv open /proc/net/dev and get network informations.
After that it initialize the server:
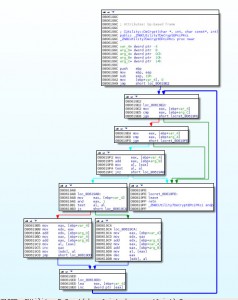
Lock at the decrypt fonction:
Decrypt fonction as call twice, one with the argument 281-206-3//18 (the C&C ip adress?), decrypt value is 190.115.20.27, and after with 68961 as the port number 59870.
Not necesseray to make a script to reverse this fonction, we can see decrypt values in memory, but this function is easy to understand, it make one ascii addition of the crypted value, after ascii soustraction and loops.
# netstat -laputen
Connexions Internet actives (serveurs et établies)
Proto Recv-Q Send-Q Adresse locale Adresse distante Etat User Inode PID/Program name
tcp 4 0 192.168.1.69:46730 190.115.20.27:59870 ESTABLISHED 1000 138545 18345/disknyp
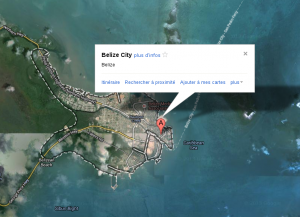
Localisation of the c&c:
Belize, it’s not the right place for make malware, but rather to jump into the see and drink mojitos 🙂
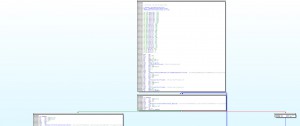
After, it call _ZN8CManager15StartNetProcessEv fonction, who create a thread, initialize a socket, and send information.
And it create an fake.cfg file, it’s containt the ip adress of my hosts, corresponding for me to the local adress.
$ cat fake.cfg
0
127.0.1.1:127.0.1.1
10000:60000
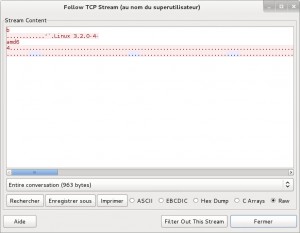
After it read /proc/stat and /proc/net/dev file and just send kernel version to the c&c in loop.

Very good analysis! And thanks for informing me at my website.
Did you see more download servers running on port 22?
best greetings,
scooba
Thanks you!
No, for the moment.
hello,I want to know what is the purpose of this sample。
According to the analysis of other experts,its only functionality is to perform DDoS attacks, mainly DNS Amplification.
I do not really understand,I hope to get detailed answers。Thank you very much……
Hi, i haven’t find any proves that’s this malware was a DNS amplifier. I think it’s a proof of concept to search servers which can be easy pown and check is bandwith.
I have to thank you for the efforts you have put
in writing this blog. I really hope to see the same high-grade content by you in the future as well.
In truth, your creative writing abilities has encouraged me to get my own, personal website now
😉